Module 5 -- Application Layer -- Computer Networks
Index
- DNS (Domain Name Space)
- DDNS (Dynamic Domain Name System)
- TELNET (TELecommunication NETwork)
- Email (Electronic Mail)
- FTP (File Transfer Protocol)
- WWW (World Wide Web)
- Hypertext Transfer Protocol(HTTP)
- SNMP (Simple Network Management Protocol)
- Bluetooth
- Firewall
- Cryptography and some basic concepts
DNS (Domain Name Space)
1. What DNS Is and Why We Need It
- Problem: Humans think in names (“openai.com”), machines route by IP (e.g.
104.18.21.89). - Solution: DNS is a distributed database that translates (resolves) human-friendly names into IP addresses, and vice versa.
Key benefits:
- Memorability: Easier to remember names than numbers.
- Flexibility: Change the IP behind a name without breaking links.
- Scalability: Distributed design handles billions of lookups per day.
2. DNS Hierarchy & Name Space
DNS is organized as a tree (a “namespace”) with these levels:
[ Root ]
|
┌─────┴─────┐
com org ← Top-Level Domains (TLDs)
| |
openai.com wikipedia.org ← Second-Level Domains
|
www.openai.com ← Subdomain / Hostname
- Root zone: Denoted by a trailing dot (
.). Root servers know all TLD servers. - TLDs:
.com,.edu, country codes (.in,.uk). - Second-level: Registrable names under a TLD (e.g.,
openai). - Subdomains: Administrative divisions (e.g.,
www,mail,api).
3. Key DNS Record Types
DNS zones hold resource records (RRs). Common ones:
| Record | Purpose |
|---|---|
| A | Maps hostname → IPv4 address |
| AAAA | Maps hostname → IPv6 address |
| CNAME | Canonical name (alias) for another name |
| MX | Mail exchanger (priority + mail server FQDN) |
| NS | Nameserver for the zone |
| TXT | Arbitrary text (SPF, DKIM, verification) |
| SRV | Service locator (protocol + port) |
| PTR | Pointer record (IP → hostname, reverse DNS) |
4. Name Resolution Process
Recursive Lookup (client asks a resolver):
- Client → Local Resolver (usually at ISP) asks “What’s
www.example.com?” - Resolver checks cache; if miss → sends query to a Root server.
- Root → tells it which TLD server to ask for
.com. - Resolver → queries the
.comTLD server; it replies with the authoritative NS forexample.com. - Resolver → asks that authoritative server; gets the A record.
- Resolver returns the IP to the client.
5. Caching & TTL
- Why cache? Reduce latency, lower load on authoritative servers.
- TTL (Time To Live): Each RR has a TTL (in seconds). Resolver caches the record until TTL expires, then must re-fetch.
- Negative caching: Failed lookups (NXDOMAIN) also cached for a shorter TTL.
2. DDNS (Dynamic DNS)
DDNS (Dynamic Domain Name System)
What It Is
DDNS is an extension of the Domain Name System (DNS) that allows automatic updates to DNS records when a device’s IP address changes dynamically. Traditional DNS maps a domain name (e.g., example.com) to a static IP address, but many devices (like home routers) use dynamic IPs assigned via DHCP, which can change over time. DDNS ensures the domain name always points to the current IP.
How It Works
- Dynamic IP Assignment: A device (e.g., a home server or router) gets a dynamic IP from the ISP via DHCP (e.g., 192.168.1.10 today, 192.168.1.20 tomorrow).
- DDNS Client: The device or router runs a DDNS client (software or firmware) that monitors the IP address for changes.
- IP Change Detection: When the IP changes, the DDNS client sends an update to the DDNS service provider (e.g., No-IP, DynDNS).
- DNS Record Update: The DDNS provider updates the DNS record (e.g., myserver.ddns.net) to map to the new IP address.
- Resolution: When someone accesses the domain (myserver.ddns.net), DNS resolves it to the current IP, ensuring uninterrupted access.
Key Components
- DDNS Provider: A service (e.g., No-IP, DynDNS) that hosts the DNS records and allows dynamic updates.
- DDNS Client: Software on the device (or built into a router) that communicates IP changes to the DDNS provider.
- DNS Server: Updates the A record (address record) to reflect the new IP.
Use Case
- Remote Access: You want to access your home security camera (myserver.ddns.net) remotely, but your ISP assigns a dynamic IP to your router. DDNS ensures the domain always points to your current IP, so you can access the camera anytime.
- Small Businesses: Hosting a small website or server on a dynamic IP connection without paying for a static IP.
Advantages
- Cost-Effective: Avoids the need for a static IP, which is more expensive.
- Convenience: Maintains consistent domain access despite IP changes.
- Scalability: Works for multiple devices in a network (e.g., multiple cameras with subdomains like cam1.ddns.net, cam2.ddns.net).
Disadvantages
- Dependency on DDNS Provider: If the provider’s service goes down, updates fail, and the domain may point to an old IP.
- Security Risks: If not secured, attackers could spoof updates to redirect traffic (use secure authentication with the DDNS provider).
- Latency: Slight delay in updating DNS records (typically a few minutes).
Example
- You set up a home server with a DDNS provider (e.g., No-IP). Your domain is
myserver.no-ip.org. Your router’s IP changes from 203.0.113.1 to 203.0.113.2. The router’s DDNS client notifies No-IP, which updates the DNS record. When you accessmyserver.no-ip.orgfrom your phone, DNS resolves it to 203.0.113.2, and you connect to your server.
Key Difference from DNS
- Static DNS: Maps a domain to a fixed IP (e.g., google.com → 142.250.190.14, which rarely changes).
- DDNS: Maps a domain to a dynamic IP, updating the record automatically when the IP changes.
Quick Recap
- DDNS Purpose: Keeps domain names accessible for devices with dynamic IPs.
- Process: DDNS client detects IP change → updates DDNS provider → DNS record updated.
- Use Case: Remote access to home devices (e.g., servers, cameras).
- Pros: Cost-effective, convenient.
- Cons: Relies on DDNS provider, potential security risks.
TELNET (TELecommunication NETwork)
What It Is
TELNET is a protocol that provides remote command-line access to a device over a network. It allows a user to log into a remote system and interact with it as if they were physically present at the machine, using a terminal interface.
How It Works
-
Connection Setup: TELNET operates at the application layer and uses TCP for reliable communication, typically on port 23.
-
Client-Server Model:
- A TELNET client (e.g., on your laptop) connects to a TELNET server running on the remote device (e.g., a router or server).
- The client sends a connection request to the server’s IP address on port 23.
-
Authentication: =The user provides credentials (username and password) to log into the remote system=.
-
Command Execution: Once logged in, the user can execute commands on the remote system via a command-line interface, and the output is sent back to the client.
-
Session: The session remains active until the user logs out or the connection is terminated.
Key Characteristics
- Plaintext Communication: TELNET transmits all data, including usernames, passwords, and commands, in plaintext, making it highly insecure.
- Bidirectional: Allows two-way communication between client and server.
- Terminal Emulation: TELNET emulates a terminal, supporting various terminal types (e.g., VT100) to ensure compatibility between different systems.
Security Issue
- Lack of Encryption: Since TELNET sends data in plaintext, it’s vulnerable to eavesdropping. An attacker can intercept sensitive information (e.g., passwords) using packet-sniffing tools.
- Modern Replacement: SSH (Secure Shell) is preferred for remote access because it encrypts all communication, using port 22.
Use Case
- Legacy Systems: TELNET is sometimes used in controlled environments (e.g., within a private LAN) to manage legacy devices like old routers or servers that don’t support SSH.
- Testing: Can be used to test if a device is reachable on port 23 (e.g., troubleshooting network connectivity).
Advantages
- Simple to Use: Easy to set up and use for remote access.
- Lightweight: Minimal overhead, suitable for low-resource devices.
Disadvantages
- Insecure: No encryption, making it unsuitable for use over the Internet or untrusted networks.
- Limited Features: Lacks modern security features like authentication encryption or session integrity.
Example
- Scenario: You need to configure a router in your lab network remotely.
- Command: On your laptop, you run telnet 192.168.1.1 23 to connect to the router at IP 192.168.1.1.
- Process: The router prompts for a username and password. After logging in, you can enter commands like show config to view the router’s configuration, and the output is displayed on your screen.
- Risk: If someone on the network intercepts the traffic, they can see your credentials and commands.
Key Difference from SSH
- TELNET: Port 23, plaintext, insecure.
- SSH: Port 22, encrypted, secure (uses public-key cryptography for authentication and data encryption).
Quick Recap
- TELNET Purpose: Provides remote command-line access to devices.
- Process: Client connects to server on port 23 → user logs in → executes commands remotely.
- Use Case: Managing legacy devices in a controlled environment.
- Security: Insecure due to plaintext transmission (use SSH instead).
- Pros: Simple, lightweight.
- Cons: No encryption, vulnerable to attacks.
Email (Electronic Mail)
What It Is (I genuinely hope I don't have to elaborate this further.)
EMAIL is a system for sending and receiving messages over a network, typically the Internet. It’s a core application-layer service that allows users to exchange text, attachments, and multimedia content.
How It Works
-
Components:
- Email Client: Software used by users to send/receive emails (e.g., Outlook, Gmail app).
- Mail Servers: Handle email delivery and storage (e.g., Gmail’s SMTP server, Yahoo’s IMAP server).
- Protocols: Define how emails are sent and retrieved.
-
Key Protocols:
-
SMTP (Simple Mail Transfer Protocol):
- Used to send emails.
- Operates on TCP port 25 (or 587 with TLS for secure communication).
- Works between mail servers (e.g., sender’s server to recipient’s server) or from client to server.
-
POP3 (Post Office Protocol 3):
- Used to retrieve emails from a server to a client.
- Operates on TCP port 110 (or 995 with SSL).
- Downloads emails to the client and typically deletes them from the server (good for single-device access).
-
IMAP (Internet Message Access Protocol):
- Also used to retrieve emails.
- Operates on TCP port 143 (or 993 with SSL).
- Keeps emails on the server, allowing access from multiple devices (e.g., phone, laptop) with synchronized state (e.g., read/unread status).
-
-
Process:
-
Sending: The sender’s email client uses SMTP to send the email to their mail server (e.g., Gmail’s SMTP server). The mail server forwards it to the recipient’s mail server (e.g., Yahoo’s server) using SMTP.
-
Receiving: The recipient’s client uses POP3 or IMAP to fetch the email from their mail server. POP3 downloads and removes the email from the server, while IMAP keeps it on the server for multi-device access.
-
Delivery: The email travels through multiple servers, with DNS lookups (MX records) determining the recipient’s mail server.
-
Key Characteristics
- Asynchronous: Sender and recipient don’t need to be online simultaneously.
- Attachment Support: Emails can include files (e.g., PDFs, images) encoded in formats like MIME (Multipurpose Internet Mail Extensions).
- Security: Basic email protocols (SMTP, POP3, IMAP) are plaintext, but secure versions (e.g., SMTP with TLS, IMAP over SSL) encrypt communication.
Use Case
- Personal Communication: Sending a birthday greeting via Gmail.
- Professional Use: Sharing a project report with a colleague via Outlook.
Advantages
- Universal Access: Works across devices and platforms (e.g., phone, laptop).
- Scalability: Handles billions of emails daily.
- Multi-Device Support: IMAP allows seamless access from multiple devices.
Disadvantages
- Security Risks: Plaintext protocols are vulnerable to interception (use TLS/SSL).
- Spam: Unwanted emails can flood inboxes.
- Storage Limits: Servers may impose storage quotas (e.g., Gmail’s 15 GB free limit).
Example
- Scenario: You send an email from user1@gmail.com to user2@yahoo.com.
- Process:
- Your email client (Gmail app) uses SMTP to send the email to Gmail’s SMTP server.
- Gmail’s server uses DNS to find Yahoo’s mail server (via MX records) and forwards the email using SMTP.
- User2’s client (Yahoo Mail app) uses IMAP to retrieve the email from Yahoo’s server, keeping it on the server for access from other devices.
Key Differences
- SMTP vs. POP3/IMAP: SMTP sends emails; POP3/IMAP retrieve them.
- POP3 vs. IMAP:
- POP3: Downloads emails, deletes from server (single-device focus).
- IMAP: Keeps emails on server, syncs across devices (multi-device focus).
Quick Recap
- EMAIL Purpose: Sends and receives messages over a network.
- Protocols: SMTP (send, port 25/587), POP3 (retrieve, port 110/995), IMAP (retrieve, port 143/993).
- Process: SMTP sends email between servers; POP3/IMAP retrieves for the client.
- Use Case: Sending a report via Gmail.
- Pros: Universal, scalable, multi-device (with IMAP).
- Cons: Security risks (use TLS), spam, storage limits.
FTP (File Transfer Protocol)
File Transfer Protocol (FTP)
What It Is
FTP is an application-layer protocol used to transfer files between computers over a network. It enables users to upload, download, or manage files on a remote server.
How It Works
-
Connection Setup:
- FTP uses TCP for reliable communication.
- Operates with two connections:
- Control Connection: On port 21, used for sending commands (e.g., login, file transfer requests).
- Data Connection: On port 20 (or a random port in passive mode), used for transferring the actual files.
-
Client-Server Model:
- An FTP client (e.g., FileZilla) connects to an FTP server.
- The user authenticates with a username and password (or anonymously, if allowed).
-
Modes:
- Active Mode: The server initiates the data connection to the client (port 20 to a client port). This can fail if the client is behind a firewall/NAT.
- Passive Mode: The client initiates the data connection to a port specified by the server. More firewall-friendly and commonly used today.
-
File Transfer:
- Commands like put (upload), get (download), ls (list files), or delete are sent via the control connection.
- The actual file data (e.g., a PDF or image) is transferred over the data connection.
Key Characteristics
-
Plaintext Communication: Like TELNET, FTP sends data (including credentials) in plaintext, making it insecure.
-
Binary and ASCII Modes:
- Binary Mode: Transfers files exactly as they are (e.g., images, executables).
- ASCII Mode: Converts line endings for text files (e.g., between Windows and Unix formats).
-
Secure Alternatives:
- FTPS: FTP over SSL/TLS, adding encryption.
- SFTP: SSH File Transfer Protocol, a completely different protocol using SSH for secure transfers (port 22).
Use Case
- Website Hosting: Uploading HTML files, images, or scripts to a web server using an FTP client like FileZilla.
- File Sharing: Transferring large files between computers in a controlled network.
Advantages
- Efficient: Designed for file transfers, with support for resuming interrupted transfers.
- Widely Supported: Available on most platforms and devices.
Disadvantages
- Insecure: Plaintext transmission of credentials and data (use FTPS or SFTP for security).
- Firewall Issues: Active mode can fail due to client-side firewalls blocking incoming connections (passive mode mitigates this).
Example
- Scenario: You’re uploading a website to a hosting server.
- Process:
- Use an FTP client (e.g., FileZilla) to connect to the server: ftp.example.com on port 21.
- Log in with your username and password.
- Use the put index.html command to upload your homepage.
- The control connection (port 21) sends the command, and the data connection (port 20 in active mode, or a random port in passive mode) transfers the file.
- Risk: If someone intercepts the traffic, they can see your credentials and the file contents (use SFTP instead).
Key Difference from SFTP
- FTP: Ports 20/21, plaintext, insecure.
- SFTP: Port 22, encrypted via SSH, secure.
Quick Recap
- FTP Purpose: Transfers files between computers over a network.
- Process: Control connection (port 21) for commands, data connection (port 20 or random) for file transfers.
- Modes: Active (server-initiated data connection), Passive (client-initiated).
- Use Case: Uploading files to a web server.
- Security: Insecure (plaintext); use FTPS or SFTP for secure transfers.
- Pros: Efficient, widely supported.
- Cons: Insecure, firewall issues in active mode.
WWW (World Wide Web)
If you don't know about this, maybe get out of whatever cave you live in? Or maybe give a damn a bit about what technology you use and how it works under the hood? No? Stop learning CS then? Idk.
What It Is
The World Wide Web (WWW) is a system of interlinked hypertext documents and resources (e.g., web pages, images, videos) accessed over the Internet, typically through web browsers. It’s a core application-layer service that makes the Internet user-friendly by allowing navigation via hyperlinks.
How It Works
-
Client-Server Model:
- Web Browsers (clients, e.g., Chrome, Firefox) request resources from web servers (e.g., Apache, Nginx) hosting websites.
- Users access resources by entering a URL (e.g., https://example.com) in the browser.
-
Key Components:
- URL (Uniform Resource Locator): Identifies a resource (e.g., https://www.google.com/search).
- Hypertext: Documents (web pages) written in HTML (HyperText Markup Language) that include hyperlinks to other resources.
- Web Servers: Store and serve web content (HTML, CSS, JavaScript, images).
- Hyperlinks: Links embedded in web pages that allow navigation (e.g., clicking “About Us” takes you to another page).
-
Protocol:
- The WWW relies on HTTP/HTTPS (HyperText Transfer Protocol/Secure) for communication between clients and servers (more on HTTP in the next topic).
- HTTP operates on port 80, HTTPS on port 443 (with SSL/TLS encryption).
-
Process:
- A user enters a URL in their browser (e.g., https://example.com).
- The browser resolves the domain (example.com) to an IP address via DNS.
- The browser sends an HTTP/HTTPS request to the web server.
- The server responds with the requested resource (e.g., an HTML page), which the browser renders for the user.
Key Characteristics
- Hypertext-Based: Resources are linked via hyperlinks, enabling non-linear navigation.
- Distributed System: Content is hosted on servers worldwide, accessible globally.
- Platform-Independent: Works on any device with a browser (e.g., phone, laptop).
- Dynamic Content: Modern WWW supports interactive content via JavaScript and APIs (e.g., loading new posts on a social media feed without refreshing the page).
Use Case
- Browsing: Accessing a news article on cnn.com by entering the URL or clicking a link.
- E-Commerce: Shopping on amazon.com, where hyperlinks navigate you from product listings to checkout.
Advantages
- Ease of Use: Intuitive navigation via hyperlinks and browsers.
- Global Access: Connects users to resources worldwide.
- Rich Content: Supports text, images, videos, and interactive elements.
Disadvantages
- Security Risks: Unencrypted HTTP connections (use HTTPS for security).
- Overload: Heavy web pages with multimedia can be slow to load on low-bandwidth connections.
- Privacy Concerns: Tracking via cookies or scripts can compromise user privacy.
Example
- Scenario: You visit Google’s homepage.
- Process:
- You type https://www.google.com in your browser.
- The browser uses DNS to resolve www.google.com to an IP (e.g., 142.250.190.14).
- The browser sends an HTTPS GET request to the server.
- Google’s server responds with the HTML, CSS, and JavaScript for the homepage.
- The browser renders the page, showing the Google search bar and logo.
- Navigation: Clicking a link (e.g., “Images”) sends another request to load the Images page.
Key Difference from the Internet
- Internet: The underlying network infrastructure (e.g., TCP/IP, routers).
- WWW: An application service on the Internet, accessed via browsers using HTTP/HTTPS.
Hypertext Transfer Protocol(HTTP)
(This is also fairly common knowledge, but no judgement from me if you don't know this one)
HTTP stands for “Hypertext Transfer Protocol.” It is a set of rules for sharing data on the World Wide Web (WWW). HTTP helps web browsers and servers communicate, allowing people to access and share information over the internet.
Key Points
- Basic Structure: HTTP forms the foundation of the web, enabling data communication and file sharing.
- Web Browsing: Most websites use HTTP, so when you click on a link or download a file, HTTP is at work.
- Client-Server Model: HTTP works on a request-response system. Your browser (client) asks for information, and the website’s server responds with the data.
- Application Layer Protocol: HTTP operates within the Internet Protocol Suite, managing how data is transmitted and received.
What is HyperText?
Data such as text, images, and other multimedia files are shared on the World Wide Web.
Working of HTTP
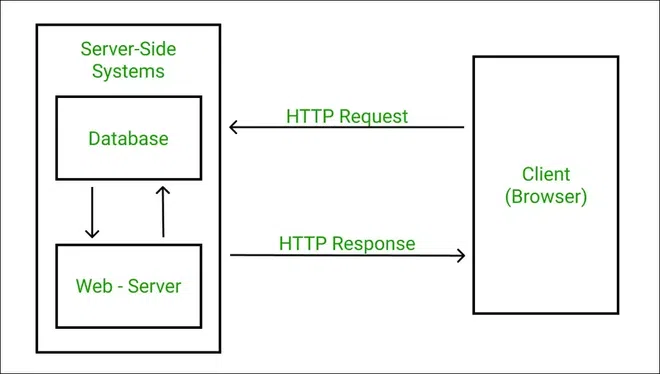
First of all, whenever we want to open any website we first open a web browser after that we will type the URL of that website (e.g., www.facebook.com ). This URL is now sent to the Domain Name Server (DNS). Then DNS first checks records for this URL in their database, and then DNS will return the IP address to the web browser corresponding to this URL. Now the browser is able to send requests to the actual server.
After the server sends data to the client, the connection will be closed. If we want something else from the server we should have to re-establish the connection between the client and the server.
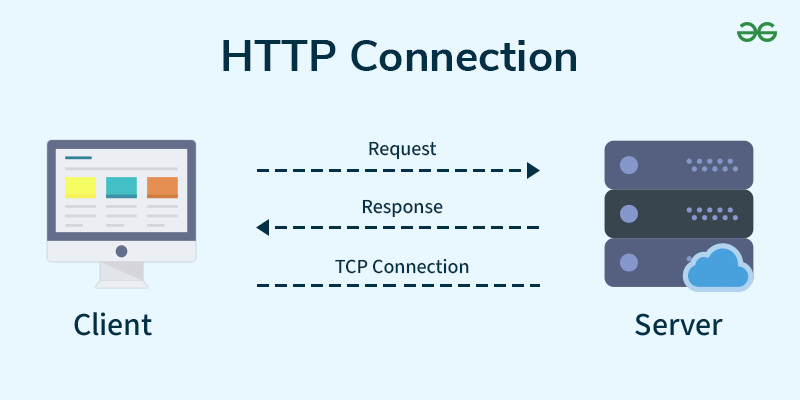
-
Client-Server Model:
- A client (e.g., a web browser like Chrome) sends an HTTP request to a server (e.g., a web server hosting example.com).
- The server responds with an HTTP response containing the requested resource (e.g., an HTML page).
-
Connection:
- HTTP uses TCP for reliable communication.
- Operates on port 80 by default.
- HTTPS (HTTP Secure) is the encrypted version, using SSL/TLS, and operates on port 443.
-
Request-Response Cycle:
- Request: The client sends a message with a method, URL, headers, and optional body.
- Example: GET /index.html HTTP/1.1 (requests the homepage).
- Response: The server replies with a status code, headers, and the requested resource.
- Example: HTTP/1.1 200 OK (success, followed by the HTML content).
- Request: The client sends a message with a method, URL, headers, and optional body.
-
Stateless Protocol:
- HTTP is stateless, meaning each request is independent. The server doesn’t remember previous requests unless mechanisms like cookies or sessions are used.
What is an HTTP Request?
HTTP request is simply termed as the information or data that is needed by Internet browsers for loading a website. This is simply known as HTTP Request.
There is some common information that is generally present in all HTTP requests. These are mentioned below.
- HTTP Version
- URL
- HTTP Method
- HTTP Request Headers
- HTTP Body
HTTP Request Headers
HTTP Request Headers generally store information in the form of key-value and must be present in each HTTP Request. The use of this Request Header is to provide core information about the client’s information, etc.
HTTP Request Body
HTTP Request Body simply contains the information that has to be transferred. HTTP Request has the information or data to be sent to these browsers.
What is HTTP Response?
HTTP Response is simply the answer to what a Server gets when the request is raised. There are various things contained in HTTP Response, some of them are listed below.
- HTTP Status Code
- HTTP Headers
- HTTP Body
HTTP Response Headers
HTTP Response headers are simply like an HTTP Request where it has that work to send some important files and data to the HTTP Response Body.
HTTP Response Body
HTTP Responses are the responses that are received successfully upon the request. Generally, it comes under the requests generated by the web. In most cases, the request is to transfer the HTML data into a webpage.
What is an HTTP Status Code?
HTTP Status Codes are the 3-digit codes that tell the message or simply tell us about the HTTP Request whether it has been completed or not. There are simply 5 types of status codes.
- 1xx (Informational): Request received, processing (e.g., 100 Continue).
- 2xx (Success): Request successful (e.g., 200 OK).
- 3xx (Redirection): Resource moved (e.g., 301 Moved Permanently).
- 4xx (Client Error): Client-side error (e.g., 404 Not Found, 403 Forbidden).
- 5xx (Server Error): Server-side error (e.g., 500 Internal Server Error).
Key Methods
- GET: Retrieve a resource (e.g., load a webpage).
- POST: Submit data to the server (e.g., form submission, like logging into a website).
- PUT: Update a resource on the server.
- DELETE: Remove a resource.
- HEAD: Retrieve only the headers of a resource (no body, used for metadata).
HTTPS (Secure Version)
- What It Is: HTTP over SSL/TLS, ensuring encrypted communication.
- Why It’s Needed: HTTP sends data in plaintext, making it vulnerable to interception (e.g., man-in-the-middle attacks). HTTPS encrypts the data, protecting sensitive information like passwords or credit card details.
- How It Works:
- Uses SSL/TLS certificates issued by Certificate Authorities (CAs) to verify the server’s identity.
- Establishes an encrypted connection via a handshake (e.g., exchanging public keys).
Use Case
- Browsing: When you visit https://example.com, your browser uses HTTPS to request the homepage, and the server responds with the HTML content.
- Form Submission: Submitting a login form via a POST request to authenticate with a website.
Advantages
- Simplicity: Easy to implement and use for web communication.
- Flexibility: Supports various methods (GET, POST, etc.) and media types (HTML, images, JSON).
- Ubiquitous: Supported by all web browsers and servers.
Disadvantages
- Statelessness: No memory of previous requests (requires cookies/sessions for persistence).
- Insecure (HTTP): Plaintext transmission (use HTTPS for security).
- Overhead (HTTPS): Encryption adds computational overhead, though modern hardware handles it well.
Example
- Scenario: You visit a website.
- Process:
- You enter https://example.com in your browser.
- The browser resolves the domain to an IP via DNS.
- The browser sends an HTTPS request: GET / HTTP/1.1 Host: example.com.
- The server responds: HTTP/1.1 200 OK, followed by the HTML content of the homepage.
- The browser renders the page for you to view.
- Security: With HTTPS, the communication is encrypted, so an attacker can’t intercept your data.
Key Difference from FTP
- HTTP: Transfers hypertext (web content), stateless, port 80/443.
- FTP: Transfers files, stateful (maintains a session), ports 20/21.
SNMP (Simple Network Management Protocol)
The Internet is a vast and dynamic network of interconnected devices. To keep this complex system running smoothly, network administrators need a way to monitor, configure, and troubleshoot all the different pieces of equipment. This is where SNMP (Simple Network Management Protocol) comes in.
The Concept of SNMP: Your Network's Health Monitor and Control System
Imagine you're managing a large factory with many different machines: some are for production, some are for packaging, some are for quality control, etc. You can't run to each machine individually every time to check its status, change a setting, or see if it's having a problem. You need a central way to oversee and control them.
SNMP is essentially the universal language and system that allows network administrators to monitor and manage network devices from a central location. It's like having a control panel for your entire network factory.
Why is SNMP Needed?
Networks are made up of devices from many different manufacturers (Cisco routers, HP switches, Dell servers, Canon printers, etc.). Without a common protocol, every device would speak a different "language," making centralized management impossible. SNMP provides that common language.
It allows you to:
- Monitor Performance: Check how busy a router is, how much bandwidth a switch port is using, how many pages a printer has printed, etc.
- Detect Issues: Get alerts when a device runs out of toner, a server's CPU usage spikes, or a network link goes down.
- Configure Devices: Remotely change settings on a device (though this is used with caution due to security implications).
- Troubleshoot Problems: Gather data to diagnose why a part of your network might be slow or failing.
Key Components of SNMP:
SNMP works with a few key players:
-
SNMP Manager (or Network Management System - NMS):
- Analogy: This is the factory supervisor's desk or the main control room.
- Role: It's the central computer or software application that runs the SNMP management software. It sends requests to network devices, receives their responses, and processes alerts. This is where the network administrator sits to manage everything.
-
SNMP Agent:
- Analogy: This is a small, dedicated assistant (or sensor) built into each machine on the factory floor.
- Role: It's a software program that runs directly on a network device (like a router, switch, server, or printer). The agent collects information about its host device, stores it, and makes it available to the SNMP Manager. It can also send alerts.
-
Managed Devices:
- Analogy: These are the individual machines in the factory (e.g., the production machine, the packaging machine).
- Role: Any network device that has an SNMP agent running on it and can be managed by an SNMP Manager. This includes routers, switches, servers, firewalls, printers, IP phones, etc.
-
Management Information Base (MIB):
- Analogy: This is the instruction manual or blueprint specific to each machine. It lists all the things that can be monitored or controlled on that particular machine, along with what that information means.
- Role: It's a standardized database (hierarchical in structure) that defines the variables (data points) that an SNMP agent can access or control on a managed device. Each variable has a unique identifier (called an OID - Object Identifier). For example, a MIB might define an OID for "CPU utilization," "interface error count," or "printer toner level."
-
SNMP Messages (the communication methods):
- Analogy: These are the ways the supervisor (Manager) and assistants (Agents) communicate.
GETRequest: Manager asks agent for specific information (e.g., "What is the CPU usage?").GET NEXTRequest: Manager asks agent for the next piece of information in a list (e.g., "Give me the next port's traffic data.").SETRequest: Manager tells agent to change a setting on the device (e.g., "Change this port's status to disable." - used less often due to security).TRAP(orINFORM): Agent proactively sends an alert to the Manager when something important happens (e.g., "Warning! Toner is low!" or "Critical! Network interface went down!"). Traps are one-way, while Informs require an acknowledgment.
How SNMP Works (A Simple Flow):
-
Initialization: Network administrator sets up an SNMP Manager and configures SNMP agents on all relevant network devices. They also specify a "community string" (like a simple password) for authentication between manager and agent.
-
Manager Requests Data: The SNMP Manager sends
GETrequests to the agents on managed devices. -
Agent Responds: The agent retrieves the requested information from its MIB and sends it back to the Manager.
-
Manager Processes Data: The Manager collects this data, displays it on dashboards, logs it, and can trigger actions (e.g., send an email alert if a threshold is crossed).
-
Agent Sends Alerts: If a critical event occurs on a device (e.g., a link failure), the agent proactively sends a
TRAPmessage to the Manager to notify it immediately.
In essence, SNMP provides the eyes and ears (monitoring) and sometimes the hands (configuration) for network administrators, allowing them to effectively manage and maintain the health of complex networks.
Bluetooth
(I am pretty sure you have heard of this one)
What is Bluetooth?
Imagine you have a bunch of small electronic gadgets (like your phone, headphones, a fitness tracker, a smart speaker, or even your car). Traditionally, connecting these gadgets often meant dealing with messy cables.
Bluetooth is a short-range, wireless technology that allows two or more devices to connect and exchange data with each other over very short distances, without the need for cables.
- It's designed for convenience, low power consumption, and to replace those annoying wires for simple connections.
Why Was Bluetooth Created? (The Problem It Solves)
The main goal of Bluetooth was to get rid of cables for simple, everyday connections between devices. Think about:
- Connecting wireless headphones to your phone.
- Linking your phone to your car's stereo.
- Using a wireless mouse or keyboard with your computer.
- Sharing a picture quickly with a friend nearby.
Before Bluetooth, these often required specific cables or complicated infrared connections.
Key Concepts of Bluetooth:
-
Short-Range Wireless:
-
Analogy: Think of it like a very quiet conversation between two people standing close to each other. You can hear them perfectly, but someone across the room (or in the next room) can't.
-
Reality: Bluetooth typically works reliably up to about 10 meters (33 feet), though some powerful versions can go further. It's not for connecting devices across your house, let alone across the Internet.
-
-
Low Power Consumption:
-
Analogy: It's like using a small battery-operated toy, not a high-power appliance.
-
Reality: Bluetooth is designed to use very little battery power, which is why it's perfect for small devices like earbuds, smartwatches, and fitness trackers that need to last a long time on a single charge.
-
-
Wireless Personal Area Network (WPAN):
-
Analogy: It's like creating a tiny, exclusive club around one person or device, where only a few selected friends (other Bluetooth devices) can join.
-
Reality: When Bluetooth devices connect, they form a small network called a "piconet." One device acts as the "master" (e.g., your phone), and up to seven other devices can be "slaves" (e.g., headphones, watch, car).
-
-
Frequency Hopping Spread Spectrum (FHSS):
-
Analogy: Remember FHSS in Spread Spectrum? Bluetooth uses this! It's like two people having a conversation by rapidly jumping between different radio channels, following a secret, pre-arranged sequence. If someone else tries to listen or interfere, they just hear static because they don't know the jumping pattern.
-
Reality: Bluetooth devices constantly change (hop) frequencies within the 2.4 GHz radio band. This helps it avoid interference from Wi-Fi (which uses the same band) and makes the connection more robust and secure.
-
-
Pairing:
-
Analogy: This is like introducing two friends to each other and giving them a secret handshake. Once they've learned the handshake, they can easily recognize and talk to each other whenever they meet again.
-
Reality: When you connect two Bluetooth devices for the first time (e.g., headphones to your phone), they go through a "pairing" process. This involves exchanging security keys so they can recognize and trust each other in the future. You often need to put one device into "pairing mode" and select it on the other.
-
-
Profiles:
-
Analogy: Once two devices are paired, they can perform specific "roles" or "jobs" together. A "Headphone Job" is different from a "File Sharing Job."
-
Reality: Bluetooth devices use "profiles" to define how they will communicate for specific tasks. For example, the "A2DP" profile defines how stereo audio is streamed, while the "HFP" profile defines how a headset handles phone calls. Both devices must support the same profile for a specific function to work.
-
How Bluetooth Works (Simplified Flow):
- Discovery: Your phone (or other device) scans for nearby Bluetooth devices that are "discoverable" (broadcasting their presence).
- Pairing: You select the device you want to connect to. They exchange security codes (sometimes requiring you to enter a PIN), creating a trusted bond.
- Connection: Once paired, they can establish a connection and begin communicating.
- Data Exchange: Based on the supported profiles, they can start sending and receiving data for their specific task (e.g., audio to headphones, contact list to a car, health data to a fitness app).
Common Uses of Bluetooth:
- Wireless Audio: Headphones, speakers, car audio systems.
- Peripherals: Keyboards, mice, game controllers.
- File Sharing: Quickly sending small files between nearby phones/computers (though Wi-Fi Direct is often faster for larger files).
- Smart Devices: Fitness trackers, smartwatches, some IoT (Internet of Things) devices.
- Hands-free Calling: Connecting phones to car systems or headsets.
In essence, Bluetooth is the handy, low-power, short-range wireless solution for connecting your personal gadgets and making your digital life a bit more cable-free!
Firewall
What is a Firewall?
Imagine your computer or your entire home/office network as a house or a fortress. This house contains all your valuable possessions (your data, personal information, sensitive files). Outside, there's a vast, unpredictable world (the Internet) with many potential threats, some friendly, some not so much.
A Firewall is like a security guard or a gatekeeper stationed at the main entrance (or entrances) of your house/network. Its primary job is to control who and what can go in and out, based on a set of rules you've given it.
- It's a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
Why is a Firewall Needed? (The Problem It Solves)
The Internet is a public place. Without a firewall, your computer or network is directly exposed to everything out there:
- Malicious Software (Malware, Viruses, Worms): Programs designed to harm your system, steal data, or spy on you.
- Hackers: Individuals trying to gain unauthorized access to your devices to steal information, disrupt services, or use your computer for their own nefarious purposes.
- Unwanted Traffic: Just annoying or bandwidth-consuming traffic that you don't need or want.
A firewall acts as your first line of defense, preventing these threats from reaching your valuable resources or stopping your sensitive data from leaving without permission.
How a Firewall Works (The Gatekeeper's Job):
The core of a firewall's operation is its rule set or security policy. These are like instructions given to the security guard.
-
Inspect Every Packet: Every single piece of data (packet) trying to enter or leave your network must pass through the firewall. The firewall examines each packet's header.
- Analogy: Every person trying to enter or leave your house must stop at the gate and show their ID, package, or reason for being there.
-
Apply Rules: The firewall compares the information in the packet's header (like source IP address, destination IP address, port number, protocol type – think of these as the person's name, where they're going, what they're carrying, and what they're doing) against its predefined rules.
- Analogy: The security guard checks the person's ID and purpose against a list of rules: "Are they on the 'allowed visitors' list?", "Are they trying to enter a restricted area?", "Are they bringing in anything suspicious?"
-
Decision: Allow or Deny:
- If the packet matches a rule that says "ALLOW," it passes through.
- If it matches a rule that says "DENY" (or no "ALLOW" rule is matched, and the default is "DENY"), the packet is blocked or dropped.
- Analogy: If the person matches an "allow" rule, the guard opens the gate. If they match a "deny" rule, or don't match any "allow" rule, the guard keeps the gate shut and turns them away.
Key Functions/Types of Firewalls:
Firewalls come in different types, offering varying levels of scrutiny:
-
Packet-Filtering Firewalls (The Basic Guard):
-
How it works: This is the most basic type. It inspects packets individually, looking only at their headers (source/destination IP, port numbers, protocol). It doesn't remember previous packets or context.
-
Analogy: A very strict guard who only looks at the ID and the immediate purpose. They don't remember if this person just entered five minutes ago or if they're part of an ongoing conversation.
-
Example: "Allow all traffic from my internal network to the web (port 80/443), but block all incoming connections on port 22 (SSH) from outside."
-
-
Stateful Inspection Firewalls (The Smart Guard with a Memory):
-
How it works: This is the most common type today. It not only inspects headers but also keeps track of the "state" of connections. If you initiate an outgoing connection (e.g., Browse a website), it remembers that connection and automatically allows the incoming response packets, even if there isn't an explicit rule for them.
-
Analogy: A smart guard who remembers that when you leave to get a pizza, he should expect you to return with a pizza box. If you come back with a suspiciously large, unlabeled crate instead, he'll question it, even if he didn't explicitly have a rule for "large unlabeled crates."
-
Benefit: Much more secure and efficient for legitimate traffic because it understands context.
-
-
Application-Layer Firewalls / Proxy Firewalls / Next-Generation Firewalls (The Deep Inspector):
-
How it works: These are the most advanced. They don't just look at headers; they can inspect the actual content of the data traffic, understand specific applications (like HTTP, FTP), and even look for malware signatures. Some act as proxies, intercepting and inspecting the entire connection before forwarding it.
-
Analogy: A highly trained security team that not only checks IDs but also inspects the contents of packages, scans for contraband, and can even understand the language of a conversation to detect suspicious activity. They might also make you put your package through an X-ray scanner before they let it through.
-
Benefit: Offers much more granular control and protection against sophisticated threats.
-
Types of Firewalls by Location:
-
Network-based Firewalls (Hardware Appliances): These are dedicated hardware devices placed at the border between your network and the Internet (or between different segments of a large network).
- Analogy: The main security gate for the entire office building.
-
Host-based Firewalls (Software Firewalls): These are software programs installed directly on individual computers (like Windows Firewall or macOS Firewall).
- Analogy: A personal security guard standing right at the door of your specific office within the building. Even if someone gets past the main gate, they still have to get past your personal guard.
In essence, a firewall is your essential digital security guard, diligently enforcing rules to protect your network from unwanted visitors and harmful intrusions, allowing only the legitimate and desired traffic to pass through.
Cryptography and some basic concepts
Alright, let's unlock the secrets of Cryptography!
What is Cryptography?
Imagine you want to send a secret message to a friend, but you know there's a nosy person who might intercept your message. How do you make sure only your friend can read it? You come up with a secret code or a cipher.
Cryptography is the art and science of secure communication in the presence of adversaries. In simpler terms, it's about making information secret, verifying its authenticity, and ensuring it hasn't been tampered with, even if someone else gets their hands on it.
The word "cryptography" comes from Greek words:
- "Kryptos" meaning "hidden" or "secret"
- "Graphein" meaning "to write"
So, literally, "secret writing."
Why is Cryptography Needed? (The Goals of Security)
In the digital world, cryptography isn't just for spies. It's fundamental to almost everything we do online. It aims to achieve several critical security goals:
-
Confidentiality (Secrecy/Privacy):
- Goal: To ensure that only authorized people can read or access sensitive information.
- Analogy: Putting your secret message in a locked box and only giving the key to your trusted friend. Even if someone else gets the box, they can't open it.
- Real-world: Protecting your online banking details, private emails, medical records, etc.
-
Integrity:
- Goal: To ensure that information has not been altered, damaged, or tampered with during storage or transmission.
- Analogy: Putting a special tamper-evident seal on your locked box. If the seal is broken when your friend receives it, they know someone tried to mess with the contents.
- Real-world: Verifying that a downloaded software update hasn't been infected with a virus, or that a financial transaction amount hasn't been changed.
-
Authentication:
- Goal: To verify the identity of the sender or receiver; proving that the person you're communicating with is who they claim to be.
- Analogy: Your friend has a unique secret handshake or a special ID badge that only you two know. When someone claims to be your friend, they must perform the handshake or show the badge to prove their identity.
- Real-world: Logging into your email account with a password, verifying a website's identity (the padlock icon in your browser).
-
Non-repudiation:
- Goal: To ensure that a sender cannot legitimately deny having sent a message, and a receiver cannot deny having received it. It provides proof of origin.
- Analogy: When you sign a legal document, your signature is unique proof that you agreed to it. You can't later say, "I never signed that."
- Real-world: Digital signatures on contracts or emails, proving that a specific payment instruction came from your bank.
Basic Concepts and Techniques in Cryptography:
1. Encryption and Decryption:
-
Encryption: The process of converting readable information (called plaintext or cleartext) into an unreadable, scrambled form (called ciphertext).
-
Decryption: The process of converting ciphertext back into readable plaintext.
-
Key: This is the most crucial part! A key is a piece of secret information (like a password or a long string of random bits) that is used by an algorithm to perform encryption and decryption. Think of it as the combination to the lock on your secret box.
2. Types of Encryption:
a. Symmetric-key Cryptography (Shared Secret Key):
-
How it works: This uses a single, shared key for both encryption and decryption. Both the sender and the receiver must have this identical secret key.
-
Analogy: You and your friend both have the exact same key to the same padlock. You lock the message in the box with your key, and your friend uses their identical key to unlock it.
-
Pros: It's generally very fast for encrypting and decrypting large amounts of data.
-
Cons: The biggest challenge is key distribution. How do you securely share that secret key with your friend in the first place, without the nosy person intercepting the key itself?
-
Examples: AES (Advanced Encryption Standard), DES (Data Encryption Standard - older and less secure now).
- Asymmetric-key Cryptography (Public-key Cryptography):
-
How it works: This uses a pair of mathematically linked keys: a public key and a private key.
-
Your public key can be freely given to anyone, published, or listed in a directory.
-
Your private key must be kept absolutely secret and only known to you.
-
If you encrypt a message with someone's public key, only their corresponding private key can decrypt it.
-
If you encrypt a message with your own private key, anyone can decrypt it with your public key, but it proves you sent it (used for digital signatures!).
-
Analogy: Imagine a special padlock system. You have a padlock with two keys. One is a special "locking key" (your public key) that you can give to anyone. Anyone can lock something with it. The other is an "unlocking key" (your private key) that only you possess. No one else can unlock what your locking key secured.
-
Pros: Solves the key distribution problem. You don't need to secretly share anything beforehand to send encrypted messages. Also used for digital signatures for authentication and non-repudiation.
-
Cons: It's computationally much slower than symmetric-key cryptography, so it's typically used for smaller tasks like securely exchanging the symmetric key itself, or for digital signatures.
-
Examples: RSA, ECC (Elliptic Curve Cryptography).
3. Hashing (Data Fingerprinting):
-
How it works: A hash function takes any input data (of any size) and produces a fixed-size, unique "fingerprint" called a hash value or digest. It's a one-way function, meaning you can't reverse-engineer the original data from the hash.
-
Analogy: Like taking a document and running it through a shredder that always produces the same length of confetti for that exact document. If even one letter changes in the document, the confetti pattern will be completely different. You can't put the confetti back together to get the document.
-
Purpose: Primarily used for integrity (checking if data has been altered) and password storage (storing hash of password instead of actual password).
-
Examples: SHA-256, MD5 (older and less secure for some uses).
In summary, cryptography is the powerful set of tools and techniques that underpin digital security, allowing us to communicate and transact online with confidence that our information is private, authentic, and untampered with.