Module 1 -- Introduction to Cyber Security
Index
- Introduction to Cyber Security
- Importance and challenges in Cyber Security
- Cyberspace
- Cyber threats
- Cyberwarfare
- CIA Triad
- Cyber Terrorism
Introduction to Cyber Security
1. Foundational Concepts
What You Need to Know First
Before diving into cyber security, it's essential to understand some fundamental concepts:
- Computer Systems: A computer system consists of hardware (physical components) and software (programs). Hardware includes CPUs, memory, storage devices, input/output devices, and networks.
- Networks: A network is a collection of interconnected devices that can communicate with each other. Networks can be local (LAN), wide-area (WAN), or the internet.
- Data: Data refers to the information stored in computer systems. It can be structured (e.g., databases) or unstructured (e.g., files).
- Threats: A threat is a potential danger or risk to a computer system, network, or data.
Key Terms
- Vulnerability: A weakness in a computer system, network, or application that can be exploited by an attacker.
- Exploit: A piece of code or technique used to take advantage of a vulnerability and compromise the system.
- Attack: An attempt to breach or disrupt a computer system, network, or data.
2. The Intuition
A Real-World Analogy
Imagine your home is a computer system, and you're trying to protect it from unwanted visitors (hackers). You install locks on the doors (firewalls), keep valuable items in a safe (encrypt sensitive data), and use security cameras (monitor network traffic) to detect any suspicious activity. This analogy will help ground abstract concepts in concrete terms.
3. Step-by-Step Breakdown with Examples
The Core Mechanics
Cyber security involves several steps:
- Identify: Identify the assets that need protection, such as computer systems, networks, or data.
- Assess: Assess the risks and vulnerabilities associated with these assets.
- Mitigate: Implement controls to reduce the likelihood of a threat occurring (e.g., install firewalls, use strong passwords).
- Detect: Monitor for suspicious activity and detect potential threats.
- Respond: Respond quickly and effectively in case of a breach or attack.
Example 1: Identifying Assets
Suppose you're responsible for securing a small business with 10 employees. The assets to protect are:
- 2 servers (file server and database server)
- 10 workstations
- Network infrastructure (switches, routers)
- Employee data (names, addresses, social security numbers)
Example 2: Assessing Risks
Let's assume you've identified the assets. Next, assess the risks associated with each asset:
- Server 1: High risk due to its role in storing sensitive customer information.
- Workstations: Medium risk due to their potential for malware infection.
- Network infrastructure: Low risk since it's primarily used for communication.
Example 3: Mitigating Risks
Implement controls to reduce the likelihood of a threat occurring:
- Install firewalls on servers and workstations.
- Use strong passwords (minimum 12 characters) and enable two-factor authentication.
- Implement regular software updates and patching.
4. Key Concepts and Formulae
Important Definitions and Tools
Key Terms
- Firewall: A network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules.
- Encryption: The process of converting plaintext data into unreadable ciphertext to protect it from unauthorized access.
Formulae
- Hash Function: A one-way mathematical function that takes input data (plaintext) and produces a fixed-size output (ciphertext).
5. Applications and Relevance
Real-World Uses
Cyber security is crucial in various industries, such as:
- Finance: Protecting customer financial information and transactions.
- Healthcare: Safeguarding patient records and medical devices.
- Government: Securing sensitive information and infrastructure.
Connection to Machine Learning
Machine learning plays a significant role in cyber security:
- Anomaly Detection: Using machine learning algorithms to identify unusual patterns in network traffic or system behavior, indicating potential threats.
- Predictive Maintenance: Applying machine learning to predict when systems or networks are likely to fail, allowing for proactive maintenance and reducing downtime.
6. Common Pitfalls and Considerations
Key Takeaways
Common pitfalls to avoid:
- Insufficient Training: Failing to provide adequate training on cyber security best practices.
- Lack of Incident Response Planning: Not having a plan in place for responding to incidents or breaches.
- Inadequate Patching: Neglecting to regularly update and patch software vulnerabilities.
7. The Final Takeaway
Key Summary
Cyber security is the process of using best practices to protect computer systems, networks, and data from digital attacks. By understanding foundational concepts, identifying assets, assessing risks, mitigating threats, and applying machine learning techniques, you can effectively secure your digital presence.
Remember: Cyber security is an ongoing effort that requires continuous monitoring, assessment, and improvement to stay ahead of evolving threats.
Importance and challenges in Cyber Security
The Intuition
A Real-World Analogy
Imagine your home as a digital fortress. You have valuable possessions (data) stored within its walls (networks). Just like you would take measures to secure your physical home with locks, alarms, and surveillance cameras, cyber security involves implementing similar measures to safeguard your digital assets.
Step-by-Step Breakdown with Examples
The Core Mechanics
To understand the importance of cyber security, let's examine a hypothetical scenario:
Suppose a company, "ABC Inc.," has an online database containing sensitive customer information (e.g., names, addresses, and credit card numbers). To protect this data, ABC Inc. implements various security measures:
- Network Segmentation: Divide the network into smaller segments to limit access and reduce the attack surface.
- Firewall Configuration: Set up a firewall to block unauthorized incoming and outgoing traffic.
- Encryption: Use encryption algorithms (e.g., SSL/TLS) to scramble sensitive data, making it unreadable without the decryption key.
- Access Control: Implement user authentication and authorization mechanisms to restrict access to specific systems or data.
Let's illustrate these steps with a numerical example:
Example: ABC Inc.'s online database contains customer information. To protect this data, they implement network segmentation, configure their firewall, encrypt sensitive data, and control access.
| Step | Description | Example |
|---|---|---|
| 1. Network Segmentation | Divide the network into smaller segments to limit access and reduce the attack surface. | ABC Inc. creates a dedicated segment for customer information, limiting access to authorized personnel. |
| 2. Firewall Configuration | Set up a firewall to block unauthorized incoming and outgoing traffic. | The company configures its firewall to only allow specific IP addresses and ports for legitimate data transfer. |
| 3. Encryption | Use encryption algorithms (e.g., SSL/TLS) to scramble sensitive data, making it unreadable without the decryption key. | ABC Inc. encrypts customer information using a secure protocol like HTTPS. |
| 4. Access Control | Implement user authentication and authorization mechanisms to restrict access to specific systems or data. | The company sets up multi-factor authentication (MFA) for authorized personnel, ensuring only those with proper clearance can access the database. |
Key Concepts and Formulae
Important Definitions and Tools
- Threat: A potential vulnerability or weakness that could be exploited by an attacker.
- Vulnerability: A flaw in a system, software, or hardware that could be exploited by an attacker.
- Risk: The likelihood of a threat occurring and the potential impact if it does.
Applications and Relevance
Real-World Uses
Cyber security is crucial in various industries:
- Finance: Protecting sensitive financial information, such as credit card numbers and bank accounts.
- Healthcare: Safeguarding patient data, medical records, and treatment plans.
- Government: Securing classified information, national defense systems, and critical infrastructure.
Common Pitfalls and Considerations
Key Takeaways
When implementing cyber security measures:
- Don't overlook human factors: Cyber security is not just about technology; it's also about educating users on best practices.
- Prioritize risk assessment: Identify potential threats and vulnerabilities to focus your efforts on the most critical areas.
- Stay up-to-date with evolving threats: Continuously monitor and update your cyber security measures to address emerging risks.
The Final Takeaway
Key Concept
Cyber security is not just about protecting digital assets; it's also about ensuring the integrity, confidentiality, and availability of these assets. By implementing a comprehensive cyber security strategy that includes network segmentation, firewall configuration, encryption, access control, threat analysis, risk assessment, and continuous monitoring, you can safeguard your digital fortress and maintain a strong online presence.
Remember: Cyber security is an ongoing process that requires constant vigilance and adaptation to emerging threats.
Cyberspace

The Intuition
A Real-World Analogy
Imagine you're walking through a large, virtual city called Cyberspace. This city is made up of interconnected buildings, streets, and districts, each representing different parts of the internet. Just as you need to navigate through the physical city using maps, signs, and landmarks, you need to navigate through Cyberspace using specific tools and protocols.
In this analogy, the buildings represent websites, servers, and databases, while the streets and districts represent the pathways and connections between these digital structures. As you explore Cyberspace, you'll encounter various "neighborhoods" or communities that are connected by shared interests, languages, or technologies.
Step-by-Step Breakdown with Examples
The Core Mechanics
To understand how Cyberspace works, let's break it down into a series of steps:
- Network Connection: A user connects to the internet using a device (computer, phone, etc.) and a network interface (wired or wireless).
- IP Addressing: The device is assigned an IP address by a Dynamic Host Configuration Protocol (DHCP) server or a static IP address.
- Packet Switching: Data is broken into small packets, each with its own header containing the sender's and receiver's IP addresses.
- Routing: Packets are routed through networks using routing tables and protocols like Border Gateway Protocol (BGP).
- Receiving: The receiving device reassembles the packets in the correct order.
Example:
Suppose John wants to access a website on his laptop. He connects to the internet using Wi-Fi, and his router assigns him an IP address of 192.168.1.100. When he types in the website's URL, his browser sends a request packet with his IP address as the sender and the website's IP address as the receiver.
The packet is routed through various networks until it reaches the website's server. The server receives the packet, reassembles the data, and sends a response back to John's laptop. This process happens quickly, often in milliseconds!
Numerical Example
Let's say we have three devices connected to the internet:
| Device | IP Address |
|---|---|
| Laptop A | 192.168.1.100 |
| Server B | 10.0.0.1 |
| Router C | 172.16.254.2 |
When Laptop A sends a packet to Server B, the packet would contain the following information:
- Source IP: 192.168.1.100 (Laptop A)
- Destination IP: 10.0.0.1 (Server B)
Router C would receive the packet and route it to Server B using its routing table.
Key Concepts
Important Definitions and Tools
- IP Address: A unique numerical label assigned to each device on a network.
- Packet Switching: Breaking data into small packets for efficient transmission over networks.
- Routing: Directing packets through networks using routing tables and protocols.
All can be read in more detail in Module 3 -- Network Layer -- Computer Networks
Applications and Relevance
Real-World Uses
Cyberspace is used in various industries and fields, such as:
- E-commerce: Online shopping platforms like Amazon or eBay rely on Cyberspace to connect customers with products.
- Social Media: Social media platforms like Facebook or Twitter use Cyberspace to facilitate communication between users.
- Cloud Computing: Cloud services like Google Drive or Dropbox rely on Cyberspace to store and retrieve data.
7. The Final Takeaway
Key Takeaway
Cyberspace is a complex network of interconnected systems that enables global communication and information exchange. Understanding the fundamental concepts, protocols, and challenges involved in Cyberspace is crucial for building secure, efficient, and reliable networks that support our increasingly digital lives.
Cyber threats
The Intuition
A Real-World Analogy
Imagine your home as a digital fortress. You have a secure door (firewall), strong walls (encryption), and a vigilant guard (antivirus software). However, if you leave the door unlocked (vulnerability) or forget to lock it (neglecting security updates), an attacker can easily enter your home and cause damage.
In this analogy, cyber threats are like unwanted visitors trying to gain access to your digital fortress. You need to understand what these threats are, how they work, and how to protect yourself from them.
Step-by-Step Breakdown with Examples
The Core Mechanics
Cyber threats can be categorized into several types:
- Malware: Malicious software designed to harm or exploit a system.
- Example: A virus that deletes files on your computer.
- Phishing: Social engineering attacks that trick victims into revealing sensitive information.
- Example: An email claiming to be from your bank, asking you to reveal your login credentials.
- Ransomware: Malware that encrypts your files and demands payment in exchange for the decryption key.
- Example: A ransomware attack on a hospital's computer system, demanding $10 million in exchange for restoring access to patient records.
Let's break down each type of threat:
Step-by-Step Guide
- Malware:
- Identify the malware (e.g., virus, Trojan, worm)
- Analyze how it spreads (e.g., email attachment, infected software update)
- Develop a plan to remove or contain the malware
- Phishing:
- Recognize the phishing attempt (e.g., suspicious email, fake login page)
- Verify the authenticity of the request (e.g., check the sender's email address, look for typos)
- Report the phishing attempt and change your password if necessary
- Ransomware:
- Detect the ransomware attack (e.g., unusual network activity, encrypted files)
- Isolate affected systems to prevent further spread
- Develop a plan to restore data from backups or negotiate with the attackers
Important Definitions and Tools
- Threat Intelligence: Knowledge about existing or potential threats that can be categorized into three types:
- Strategic: Long-term threats that require strategic planning.
- Operational: Short-term threats that require immediate action.
- Tactical: Real-time threats that require quick decision-making.
Applications and Relevance
Real-World Uses
Cyber threats affect various industries, including:
- Finance: Ransomware attacks on banks and financial institutions can result in significant losses.
- Healthcare: Malware attacks on hospitals can compromise patient records and disrupt medical services.
- Government: Phishing attacks on government agencies can lead to data breaches and compromised national security.
Common Pitfalls and Considerations
Real-World Challenges
Common pitfalls when dealing with cyber threats include:
- Lack of awareness: Failing to recognize the signs of a cyber attack or phishing attempt.
- Insufficient training: Not providing employees with adequate cybersecurity training.
- Outdated software: Using outdated software that is no longer supported, making it vulnerable to attacks.
The Final Takeaway
Cyber threats are malicious attempts to damage, disrupt, or gain unauthorized access to digital systems. To protect yourself, you must understand the different types of threats, recognize their signs, and develop strategies for removal or containment. Remember: awareness is key in preventing cyber attacks.
Cyberwarfare
The Intuition
A Real-World Analogy
Imagine a country's military arsenal is not made up of tanks and planes, but rather complex computer systems and networks. Just as a traditional army might engage in warfare to protect its nation, cyberwarfare involves using digital attacks to disrupt or destroy an adversary's computer systems and networks.
This analogy will help ground the abstract concepts of cyberwarfare in concrete terms.
Step-by-Step Breakdown with Examples
The Core Mechanics
Cyberwarfare typically involves a series of steps:
- Reconnaissance: Gathering information about the target's computer systems, networks, and data.
- Exploitation: Identifying vulnerabilities and exploiting them to gain access or control.
- Persistence: Maintaining access or control over the target's systems and data.
- Exfiltration: Stealing sensitive information or disrupting critical systems.
Let's work through an example:
Suppose an attacker wants to exploit a vulnerability in a company's email server. The steps would be:
- Reconnaissance: The attacker scans the company's network to identify the email server's IP address and open ports.
- Exploitation: The attacker uses a tool like Nmap to scan for vulnerabilities and finds an unpatched flaw in the email server's software.
- Persistence: The attacker installs malware on the email server, allowing them to maintain access even after the initial attack.
- Exfiltration: The attacker steals sensitive employee data or disrupts the email server, causing downtime.
Here's a numerical example:
| Step | Action | Example |
|---|---|---|
| 1 | Reconnaissance | Scanning for IP address and open ports: nmap -p 25-30 192.168.1.100 |
| 2 | Exploitation | Identifying vulnerability using Nmap: nmap -sV -p 25-30 192.168.1.100 |
| 3 | Persistence | Installing malware: msfconsole > use exploit/unix/webdav_exec |
| 4 | Exfiltration | Stealing data or disrupting email server: nc 192.168.1.100 25 -e /bin/sh |
Types of Cyberwarfare
Below are some types of cyberwarfare
1. Propaganda
The propaganda attack aims at changing the mental state of the people in the given nation. This can be achieved through dissemination of falsehood which instill hopelessness or general lack of sympathy towards the opponent.
I think we all know at this point what "propaganda" really means. I won't say much further on this here.
2. Sabotage
Sabotage can be defined as the act of finding the company’s sensitive data and putting them at risk. It includes the competitor threat, third party threat and internal malefactor threat, whereby the latter would have something to gain from the loss and or corruption of the specific information.
3. Economic Disruption
Cyber criminals aim to intimidate the computer systems belonging to the socio-economic institutions, such as banks and stock exchanges. It is common to hear instances where they pilfer money or deny people their due, inflicting immense losses economically.
4. Electrical Power Grid Attacks
Cyber threats to the power grid result in the failure of necessary systems and the destroy of structures. This can result in a lot of communication breakdowns meaning that services like texting and making a phone call are not possible.
5. Ransomware
This type of cyber attack leads to the encryption of specific data that the attackers deem essential for the organization’s functions and then ask for a ransom for the decryption of the information. Not only is this disruptive to the target but it can also fund more cyber warfare operations in kind.
6. Espionage
Another type of cyber attack includes cyber espionage whereby an attacker uses spear-phishing, brute force, and password cracking to compromise a target’s data.
7. Subversion
Subversion in cyberwarfare involves covert actions aimed at undermining or destabilizing a target from within. This can include spreading disinformation, manipulating data, planting malicious software, or exploiting insider threats to disrupt operations, erode trust, or weaken the target's infrastructure.
Examples of Cyberwarfare Attacks
-
Ransomware: The malware subgroup known as ransomware is unique in the context of cyber warfare. By twisting crucial networks or data, it disturbs the target country and has the potential to finance further cyberwarfare operations.
-
Espionage: In situations where obtaining information is the primary goal, cybercriminals may use spear-phishing, brute-force attacks, password cracking, and other forms of digital espionage to breach data, hack into supposedly secure networks, eavesdrop via spyware, or blackmail prominent figures and authorities.
-
Malware attacks: Cyberweapons such as viruses and worms may cause major power outages, communications blackouts, or shutdowns of public utilities.
-
Subversion: One could consider the use of fake news, digital propaganda, and other disinformation to contaminate the media landscape of the target nation to be part of cyber warfare, especially when combined with other measures to undermine public confidence in institutions and authorities and spread social disturbance.
How to Combat Cyber Warfare?
The problem of cyber-warfare can be solved using a combination of products, described using actuators, policies, and education. Here are some strategies:
Install a Firewall
Firewalls are used to prevent access to the network by any unauthorized person they work as a shield to networks. Internet security; They scan the incoming and outgoing traffic; they deny any unwanted data packets while at the same time controlling access to systems.
Backup Data
Conventional procedures such as backing up critical information imply that even in the event of an attack, the necessary data would still be retrievable thus limiting the negative impact of such an eventuality. Backups should be written, preferably on other physical media, or to a different network location, in order to protect them from physical harm or network compromise.
Ensure Endpoint Protection
Endpoint protection safeguards computers attached to a system for instance laptops, tablets, and mobile devices to prevent the occurrence of security threats. This entails antivirus, intrusion detection, control on devices, and control on using devices.
Regular Software Updates
Updating the software regular is beneficial in fixing vulnerabilities and avoiding new threats that may be present. The application of security patches and updates is vital in countering cyber attackers since programs that are not updated are easily attacked.
Key Concepts and Formulae
Important Definitions and Tools
- Zero-day exploit: A previously unknown vulnerability exploited before a patch is available.
- Social engineering: Manipulating individuals into divulging sensitive information or performing certain actions.
- Phishing: A type of social engineering attack that uses fake emails or messages to trick victims.
Applications and Relevance
Real-World Uses
Cyberwarfare has significant implications for:
- National security: Disrupting critical infrastructure, compromising military operations, and stealing sensitive information.
- Business: Stealing intellectual property, disrupting supply chains, and compromising customer data.
- Individuals: Identity theft, financial fraud, and personal data breaches.
Common Pitfalls and Considerations
Limitations and Challenges
- Lack of visibility: Difficulty detecting cyber attacks or understanding their scope.
- Insufficient resources: Limited budget, personnel, or technology to respond effectively.
- Evolving threats: New attack vectors and techniques emerge constantly, making it challenging to stay ahead.
The Final Takeaway
Key Takeaway
Cyberwarfare is a complex and dynamic threat that requires a deep understanding of computer systems, networks, and data. By recognizing the importance of reconnaissance, exploitation, persistence, and exfiltration, we can better prepare ourselves for the evolving threats in this domain.
CIA Triad
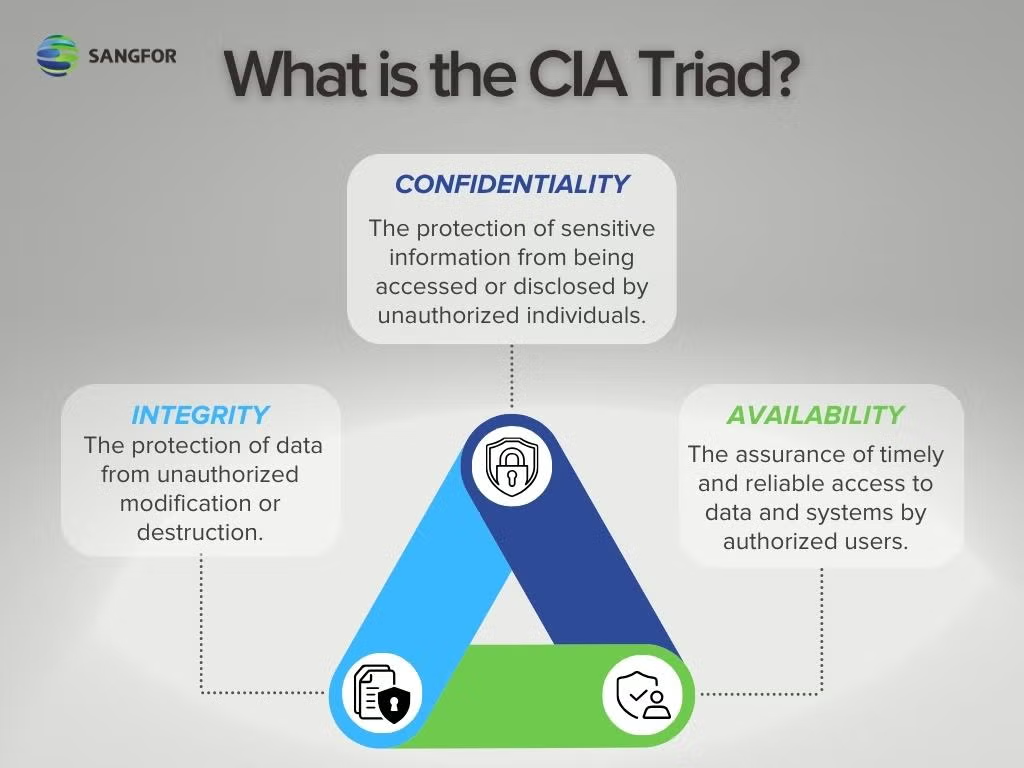
The Intuition
Imagine you're the CEO of a company that stores sensitive customer data. You want to ensure that this data remains confidential, accurate, and accessible only to authorized personnel. Think of the CIA Triad as a three-legged stool:
-
Confidentiality: The first leg represents the confidentiality aspect. Just like you wouldn't want your competitors or unauthorized individuals accessing your company's financial records, you want to protect sensitive customer data from being accessed by anyone who shouldn't have access.
-
Integrity: The second leg is integrity. This means ensuring that the data remains accurate and trustworthy. You wouldn't want your competitors tampering with your financial records or altering them in any way.
-
Availability: The third leg is availability. This ensures that authorized personnel can access the data when needed. Imagine a situation where your company's customer database becomes unavailable due to a technical issue, causing delays and lost revenue.
The CIA Triad provides a framework for understanding the fundamental goals of information security: protecting confidentiality, maintaining integrity, and ensuring availability.
Step-by-Step Breakdown with Examples
The Core Mechanics
Here's a step-by-step breakdown of the CIA Triad:
- Confidentiality:
- Identify sensitive data (e.g., customer records)
- Implement access controls (e.g., passwords, biometrics)
- Encrypt data at rest and in transit using algorithms like AES
- Limit data sharing and use need-to-know principles
Example: A company uses a password-protected database to store customer information. They encrypt the data using AES-256 and limit access to authorized personnel.
- Integrity:
- Implement authentication and authorization mechanisms (e.g., login credentials, role-based access control)
- Use digital signatures or message authentication codes (MACs) to ensure data authenticity
- Regularly back up data and store it securely off-site
Example: A company uses a digital signature to verify the authenticity of financial transactions. They also maintain regular backups of their database and store them securely off-site.
- Availability:
- Implement high-availability architectures (e.g., load balancing, redundancy)
- Use backup power sources (e.g., UPS) and redundant systems
- Regularly test disaster recovery plans
Example: A company uses a load balancer to distribute traffic across multiple servers, ensuring that the website remains available even if one server goes down. They also have a backup generator and regular disaster recovery tests.
Applications and Relevance
Real-World Uses
The CIA Triad is widely applied in various industries, including:
- Finance: Protecting sensitive financial information from unauthorized access or tampering.
- Healthcare: Ensuring patient records remain confidential and accurate.
- Government: Protecting classified information and ensuring the integrity of critical infrastructure.
Common Pitfalls and Considerations
Limitations and Challenges
Common pitfalls to avoid when implementing the CIA Triad include:
- Inadequate access controls, leading to unauthorized data breaches.
- Insufficient encryption, leaving sensitive data vulnerable.
- Neglecting regular backups and disaster recovery planning, resulting in data loss or unavailability.
The Final Takeaway
Key Takeaways
The CIA Triad provides a comprehensive framework for understanding the fundamental goals of information security: protecting confidentiality, maintaining integrity, and ensuring availability. By implementing these principles, organizations can safeguard their sensitive data and systems from various threats and vulnerabilities.
Cyber Terrorism
The Intuition
Imagine a group of hackers, motivated by political ideology, infiltrating a major power grid's control system. They manipulate the system to disrupt energy distribution, causing widespread blackouts and economic losses. This is an example of cyber terrorism in action.
The analogy highlights the potential for cyber attacks to cause significant harm, much like traditional terrorist acts. It also underscores the need for robust cybersecurity measures to prevent such attacks from occurring.
Step-by-Step Breakdown with Examples
The Core Mechanics
Cyber terrorism typically involves a combination of hacking, malware, and social engineering tactics. Here's a step-by-step breakdown of how an attack might unfold:
- Initial Infiltration: Hackers use various methods to gain access to the targeted system or network, such as exploiting vulnerabilities, using stolen credentials, or creating new accounts.
- Data Collection: The hackers gather sensitive information about the target organization, including employee data, financial records, and intellectual property.
- Malware Deployment: The attackers deploy malware, such as ransomware, Trojans, or viruses, to disrupt or destroy the target's systems and data.
- Social Engineering: Hackers use psychological manipulation to trick employees into divulging sensitive information or performing certain actions that aid the attack.
Numerical Example:
Suppose an attacker gains access to a company's email system by exploiting a vulnerability in an outdated software application. The attacker then uses this access to send phishing emails to employees, asking them to download and install malware-laced attachments. If an employee falls for the scam, the attacker can gain further access to the network.
| Step | Description |
|---|---|
| 1 | Initial Infiltration: Exploit vulnerability in email system |
| 2 | Data Collection: Gather employee data and financial records |
| 3 | Malware Deployment: Deploy ransomware to encrypt files |
| 4 | Social Engineering: Send phishing emails to employees |
Applications and Relevance
Real-World Uses
Cyber terrorism has significant implications for various industries and fields, including:
- Critical Infrastructure: Attacks on power grids, water treatment facilities, or transportation systems can have devastating consequences.
- Financial Institutions: Cyber terrorism can disrupt financial transactions, leading to economic losses and instability.
- Healthcare: Attacks on medical records or patient data can compromise sensitive information and put patients at risk.
Common Pitfalls and Considerations
Limitations and Misconceptions
Some common pitfalls to avoid when discussing cyber terrorism include:
- Underestimating the threat: Cyber terrorism is a serious concern that requires attention and resources.
- Overlooking human factors: Social engineering tactics can be just as effective as technical exploits in compromising systems.
The Final Takeaway
Cyber terrorism is a significant threat to global security, requiring a comprehensive approach to prevention and mitigation. By understanding the tactics and strategies used by cyber terrorists, we can better prepare ourselves for these attacks and protect our critical infrastructure, financial institutions, and healthcare systems.
Remember: Cyber terrorism is not just about technology; it's also about human psychology and social engineering.
Cyber Security of Critical Infrastructure
The Intuition
A Real-World Analogy
Think of critical infrastructure as a complex network of interconnected systems, like a city's transportation grid. Just as traffic flow is disrupted when one road or intersection is blocked, cyber attacks on critical infrastructure can have far-reaching consequences.
For instance, if a hospital's electronic health records (EHR) system is compromised by malware, it could lead to delays in patient care, compromising the well-being of those in need. Similarly, if a power grid's control systems are hacked, it could cause widespread blackouts and disruptions to daily life.
Step-by-Step Breakdown with Examples
The Core Mechanics
Here's a step-by-step guide to understanding the cyber security of critical infrastructure:
-
Identify Critical Assets: Determine which assets within the critical infrastructure are most vulnerable to cyber threats.
Example: A power grid operator identifies its control systems, SCADA (Supervisory Control and Data Acquisition) systems, and substation automation systems as critical assets. -
Assess Risk: Evaluate the potential risks associated with each identified asset.
Example: The power grid operator assesses the risk of a SCADA system being compromised by malware, which could disrupt power distribution and cause widespread outages. -
Implement Controls: Implement controls to mitigate identified risks.
Example: The power grid operator implements intrusion detection systems (IDS) and intrusion prevention systems (IPS) to detect and prevent malicious activity on its SCADA system. -
Monitor and Analyze: Continuously monitor and analyze the critical infrastructure's security posture.
Example: The power grid operator uses security information and event management (SIEM) systems to monitor and analyze log data from its control systems, detecting potential threats in real-time. -
Respond and Recover: Develop incident response plans and procedures for responding to and recovering from cyber attacks.
Example: The power grid operator develops an incident response plan that includes steps for isolating affected systems, containing the attack, and restoring normal operations.
Numerical Example
Let's say a hospital's EHR system is compromised by malware. The hospital's cybersecurity team needs to respond quickly to minimize the impact on patient care.
| Step | Action |
|---|---|
| 1 | Identify critical assets (EHR system) |
| 2 | Assess risk (malware could compromise patient data) |
| 3 | Implement controls (antivirus software, firewalls) |
| 4 | Monitor and analyze (SIEM system detects suspicious activity) |
| 5 | Respond and recover (isolate affected systems, restore normal operations) |
4. Key Concepts and Formulae
Important Definitions and Tools
- Risk Assessment: A systematic process for identifying, assessing, and prioritizing potential risks to critical infrastructure.
- Intrusion Detection Systems (IDS): Network-based systems that monitor network traffic for signs of unauthorized access or malicious activity.
- Intrusion Prevention Systems (IPS): Network-based systems that detect and prevent malicious activity in real-time.
5. Applications and Relevance
Real-World Uses
Cybersecurity is crucial in critical infrastructure, as it can have far-reaching consequences on public health, safety, and economic stability. For instance:
- Healthcare: Compromised EHR systems can lead to delays in patient care, compromising the well-being of those in need.
- Power Grids: Malware attacks on control systems can cause widespread power outages and disruptions to daily life.
6. Common Pitfalls and Considerations
Avoiding Common Mistakes
When implementing cybersecurity measures for critical infrastructure, it's essential to avoid common pitfalls:
- Insufficient Risk Assessment: Failing to identify potential risks can lead to inadequate security measures.
- Inadequate Incident Response Planning: Failing to develop effective incident response plans can lead to prolonged downtime and increased risk.
7. The Final Takeaway
Key Concept Summary
Cybersecurity is critical in protecting critical infrastructure, as it can have far-reaching consequences on public health, safety, and economic stability. By understanding the importance of identifying critical assets, assessing risks, implementing controls, monitoring and analyzing, responding to incidents, and recovering from attacks, we can ensure the resilience of our critical infrastructure.
Remember: Cybersecurity is not just about protecting computer systems; it's about safeguarding people's lives and livelihoods.
Cybersecurity - Organizational Implications
1. Foundational Concepts
What You Need to Know First
Before diving into organizational implications of cybersecurity, let's establish some foundational concepts.
- Organizational Security: The process of protecting an organization's assets, such as data, systems, and networks, from unauthorized access, use, disclosure, disruption, modification, or destruction.
- Risk Management: Identifying potential risks to an organization's security and implementing strategies to mitigate or manage those risks.
- Cybersecurity Frameworks: Standardized guidelines for managing cybersecurity risk, such as NIST Cybersecurity Framework (CSF) or ISO 27001.
2. The Intuition
A Real-World Analogy
Imagine a company's digital presence is like a high-security fortress. Just as you need multiple layers of defense to protect a physical fortress, an organization needs a multi-faceted approach to safeguard its digital assets.
- Network Perimeter: The outer layer of defense, protecting the organization's network from external threats.
- Intrusion Detection and Prevention Systems (IDPS): Like sentries at the gates, IDPS monitor and block suspicious traffic attempting to breach the fortress.
- Access Control: Secure doors and authentication mechanisms ensure only authorized personnel can enter the fortress.
3. Step-by-Step Breakdown with Examples
The Core Mechanics
Here's a step-by-step guide to organizational cybersecurity:
- Conduct a Security Risk Assessment (SRA): Identify potential risks and vulnerabilities in your organization's digital presence.
- Example: A fictional company, "GreenTech Inc.", conducts an SRA and finds that their outdated software is vulnerable to exploitation.
| Step | Description | Example |
|---|---|---|
| 1. Conduct SRA | Identify potential risks and vulnerabilities | GreenTech Inc. identifies outdated software as a vulnerability |
- Develop a Cybersecurity Strategy: Based on the SRA, create a plan to mitigate or manage identified risks.
- Example: GreenTech Inc.'s strategy includes updating software, implementing IDPS, and training employees.
| Step | Description | Example |
|---|---|---|
| 2. Develop Strategy | Create a plan based on SRA findings | GreenTech Inc. updates software, implements IDPS, and trains employees |
- Implement Cybersecurity Controls: Put the strategy into action by implementing controls to mitigate or manage identified risks.
- Example: GreenTech Inc. updates software, configures IDPS, and sets up access control mechanisms.
| Step | Description | Example |
|---|---|---|
| 3. Implement Controls | Execute the strategy | GreenTech Inc. updates software, configures IDPS, and sets up access control |
- Monitor and Analyze: Continuously monitor and analyze your organization's cybersecurity posture to identify potential issues and improve controls.
- Example: GreenTech Inc. monitors their system for suspicious activity and adjusts controls as needed.
| Step | Description | Example |
|---|---|---|
| 4. Monitor and Analyze | Continuously evaluate and improve cybersecurity posture | GreenTech Inc. monitors systems, adjusts controls |
4. Key Concepts and Formulae
Important Definitions and Tools
- Cybersecurity Governance: The process of overseeing and managing an organization's cybersecurity risk management.
- Incident Response Plan (IRP): A plan outlining procedures for responding to cyber-attacks or security incidents.
5. Applications and Relevance
Real-World Uses
Organizational cybersecurity is crucial in various industries, such as:
- Finance: Protecting sensitive financial information and preventing fraudulent transactions.
- Healthcare: Safeguarding patient data and ensuring continuity of care.
- E-commerce: Securing online transactions and protecting customer data.
6. Common Pitfalls and Considerations
Avoiding Common Mistakes
Common pitfalls to avoid when implementing organizational cybersecurity include:
- Insufficient Training: Failing to provide employees with adequate cybersecurity training.
- Outdated Software: Neglecting to update software, leaving vulnerabilities unaddressed.
- Inadequate Incident Response: Failing to have an effective IRP in place.
7. The Final Takeaway
Key Takeaway
Organizational cybersecurity is a crucial aspect of protecting digital assets and ensuring business continuity. By following the steps outlined above, organizations can develop a comprehensive cybersecurity strategy that includes risk management, incident response planning, and ongoing monitoring and analysis.